Tability is a cheatcode for goal-driven teams. Set perfect OKRs with AI, stay focused on the work that matters.
What are It Trainer OKRs?
The Objective and Key Results (OKR) framework is a simple goal-setting methodology that was introduced at Intel by Andy Grove in the 70s. It became popular after John Doerr introduced it to Google in the 90s, and it's now used by teams of all sizes to set and track ambitious goals at scale.
Formulating strong OKRs can be a complex endeavor, particularly for first-timers. Prioritizing outcomes over projects is crucial when developing your plans.
We've tailored a list of OKRs examples for It Trainer to help you. You can look at any of the templates below to get some inspiration for your own goals.
If you want to learn more about the framework, you can read our OKR guide online.
The best tools for writing perfect It Trainer OKRs
Here are 2 tools that can help you draft your OKRs in no time.
Tability AI: to generate OKRs based on a prompt
Tability AI allows you to describe your goals in a prompt, and generate a fully editable OKR template in seconds.
- 1. Create a Tability account
- 2. Click on the Generate goals using AI
- 3. Describe your goals in a prompt
- 4. Get your fully editable OKR template
- 5. Publish to start tracking progress and get automated OKR dashboards
Watch the video below to see it in action 👇
Tability Feedback: to improve existing OKRs
You can use Tability's AI feedback to improve your OKRs if you already have existing goals.
- 1. Create your Tability account
- 2. Add your existing OKRs (you can import them from a spreadsheet)
- 3. Click on Generate analysis
- 4. Review the suggestions and decide to accept or dismiss them
- 5. Publish to start tracking progress and get automated OKR dashboards
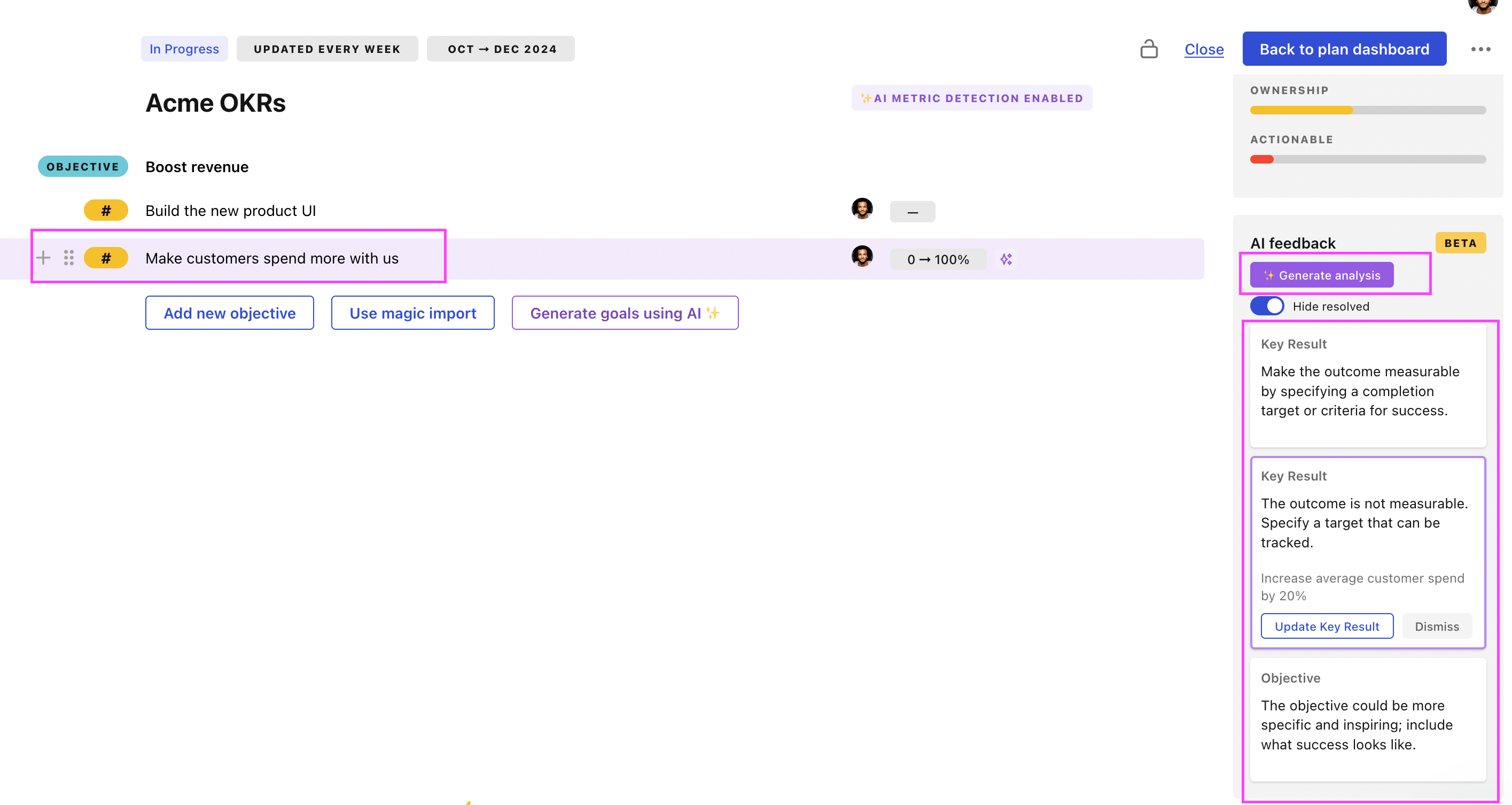
Tability will scan your OKRs and offer different suggestions to improve them. This can range from a small rewrite of a statement to make it clearer to a complete rewrite of the entire OKR.
It Trainer OKRs examples
You'll find below a list of Objectives and Key Results templates for It Trainer. We also included strategic projects for each template to make it easier to understand the difference between key results and projects.
Hope you'll find this helpful!
OKRs to enhance communication and training for Business-led IT services
ObjectiveEnhance communication and training for Business-led IT services
KRDecrease IT related issues raised by employees by 30% following the training
Implement intensive and comprehensive IT training for all employees
Establish a solid IT support team for immediate troubleshooting
Conduct regular IT performance checks and updates
KRIncrease employee trainee count by 40% in IT procedures and process
Allocate budget for training and development programs
Develop and implement strategic recruitment plans
Identify the need for additional IT trainees in the department
KRImprove post-training test scores by 25% to ensure comprehension and retention
Implement interactive learning activities during training
Offer one-on-one follow up coaching sessions
Develop comprehensive study guides for post-training review
OKRs to deploy central device management system efficiently
ObjectiveDeploy central device management system efficiently
KRComplete system development with zero critical bugs by week ten
Implement regular, rigorous bug-testing procedures
Prioritize fixing all critical bugs promptly
Outline a detailed system development plan
KRArchitect a robust system design by the end of week six
Identify necessary components for the system design
Develop preliminary blueprint for selected system architecture
Initiate system evaluation and revision process
KRTrain 75% of IT team on the system usage and troubleshooting by week twelve
Schedule and execute training sessions by week twelve
Identify members of IT team requiring system training
Develop detailed system usage and troubleshooting curriculum
OKRs to strengthen overall cybersecurity infrastructure
ObjectiveStrengthen overall cybersecurity infrastructure
KRConduct and pass two simulated cyber attacks without major system compromise
Demonstrate successful defense in a post-simulation review
Prepare and execute two different simulated cyber attack scenarios
Evaluate and address vulnerabilities exposed from the simulations
KRTrain 95% of employees on latest cybersecurity best practices
Develop a comprehensive cybersecurity training module
Conduct a needs assessment for cybersecurity training
Schedule and implement the training sessions
KRImplement multifactor authentication for all system users by end of quarter
Identify systems and platforms needing multifactor authentication
Train all system users on new authentication protocol
Select and purchase multifactor authentication software
OKRs to securely integrate Code42 and Abnormal Security with existing operations
ObjectiveSecurely integrate Code42 and Abnormal Security with existing operations
KRDevelop, test, and validate 3 playbooks for Abnormal Security integration
Write codes for 3 Abnormal Security integration playbooks
Validate the effectiveness and efficiency of each playbook
Test the functionality of all 3 playbooks
KRDefine and document 3 playbooks for Code42 integration without security breaches
Ensure secure procedures are incorporated into guides
Document the integration process explicitly
Identify necessary features for Code42 integration playbooks
KRMeasure and ensure 90% of staff are trained on the new playbooks implementation
Schedule and conduct training sessions with staff members
Conduct surveys or tests to confirm 90% staff training completion
Develop extensive training modules for new playbooks implementation
OKRs to successfully upgrade to the latest Finacle service pack
ObjectiveSuccessfully upgrade to the latest Finacle service pack
KRComplete thorough user acceptance testing with zero critical incidents found
Develop comprehensive scenarios to test all functionalities
Conduct detailed user acceptance testing
Document and address any findings promptly
KREnsure 100% of the team trained on updated system functions before deployment
Schedule mandatory training sessions for the team
Identify necessary updated system functions for training
Confirm all team members completed training
KRFully identify and document all system dependencies within two weeks
List all current system components within first week
Identify relationships and dependencies among components
Document these findings with supporting evidence
OKRs to reduce phishing incidents across all workstations
ObjectiveReduce phishing incidents across all workstations
KRImplement multi-factor authentication for all users by 80%
Purchase or develop necessary multi-factor authentication software
Train 80% of users on the new authentication method
Identify systems requiring multi-factor authentication integration
KRConduct two phishing simulation tests with 90% employee participation
Analyze and report simulation results to management
Develop and outline a comprehensive phishing simulation test
Communicate and schedule test with all employees
KRAchieve a 30% decrease in opened phishing emails through cybersecurity training
Implement strict company-wide email filtering rules
Conduct regular phishing email simulations to assess effectiveness
Develop comprehensive cybersecurity training for all staff members
OKRs to improve overall efficiency and effectiveness of data management
ObjectiveImprove overall efficiency and effectiveness of data management
KRIncrease staff proficiency in data analytics tools by conducting 3 comprehensive workshops
KRImplement automated data backup system in all databases
Schedule regular automatic system backups
Train IT staff in managing the backup system
Purchase and install reliable automated data backup software
KRReduce data processing errors by 20%
Conduct regular staff data-handling training
Implement advanced error checking software
Increase frequency of system audits
OKRs to improve IT Tech retail store deployment through automation enhancements
ObjectiveImprove IT Tech retail store deployment through automation enhancements
KRIncrease automation efficiency by 25% via software upgrades and tools integration
Implement chosen software upgrades and integrate tools
Research and select appropriate software upgrades
Identify areas of workflow that need automation improvement
KRTrain 90% of project team on new automation tools to boost deployment speed
Identify qualified trainers to teach the new automation tools
Monitor and evaluate team members' mastery of the new tools
Schedule training sessions for all project team members
KRReduce manual intervention in deployments by 30% by automating repetitive tasks
Research and implement automation tools
Train staff in using these automation tools
Identify repetitive tasks during deployments
OKRs to implement single account just-in-time access system
ObjectiveImplement single account just-in-time access system
KRIdentify and select a suitable just-in-time system solution by end of week 4
Compare features, pricing, and benefits of different systems
Choose and finalize a just-in-time system solution by end of week 4
Research just-in-time system solutions available in the market
KRAchieve 90% system usage among all staff members, ensuring successful implementation by week 12
Regularly track and report system usage throughout the week
Train all staff members extensively on system usage and functionality
Provide incentives for consistent system usage amongst staff
KROn-board and train 70% of staff on the new system by week 8
Schedule and conduct training sessions for staff members
Monitor and evaluate staff's understanding and usage regularly
Develop a comprehensive training plan for the new system
OKRs to enhance data privacy and cybersecurity measures to safeguard sensitive information
ObjectiveEnhance data privacy and cybersecurity measures to safeguard sensitive information
KRImplement a comprehensive data encryption system across all relevant platforms
Assess current data encryption measures and identify gaps for improvement
Develop and implement a standardized data encryption protocol for all platforms
Conduct regular audits to ensure consistent adherence to the data encryption system
Train employees on proper data encryption practices and its importance in data security
KRConduct regular vulnerability assessments and address identified risks within set timeframes
Quickly prioritize and address identified risks based on severity levels
Schedule regular vulnerability assessments according to established timelines
Establish set timeframes for risk mitigation and ensure timely execution
Develop a clear process for tracking and documenting vulnerability assessment findings
KRIncrease employee awareness and participation in cybersecurity training programs by 25%
Recognize and reward employees who actively participate in cybersecurity training
Create engaging and interactive modules for cybersecurity training programs
Organize lunch and learn sessions to promote employee awareness about cybersecurity threats
Send regular email reminders about upcoming cybersecurity training sessions
KRAchieve a 10% improvement in overall incident response time, ensuring timely mitigation of potential breaches
Streamline incident response processes and eliminate any unnecessary steps for faster response times
Regularly evaluate and improve incident response plans to enhance efficiency and effectiveness
Provide comprehensive training to all personnel involved in incident response procedures
Implement automation tools to expedite the identification and containment of potential breaches
It Trainer OKR best practices
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
Focus can only be achieve by limiting the number of competing priorities. It is crucial that you take the time to identify where you need to move the needle, and avoid adding business-as-usual activities to your OKRs.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
Tip #2: Commit to weekly OKR check-ins
Having good goals is only half the effort. You'll get significant more value from your OKRs if you commit to a weekly check-in process.
Being able to see trends for your key results will also keep yourself honest.
Tip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
Save hours with automated It Trainer OKR dashboards
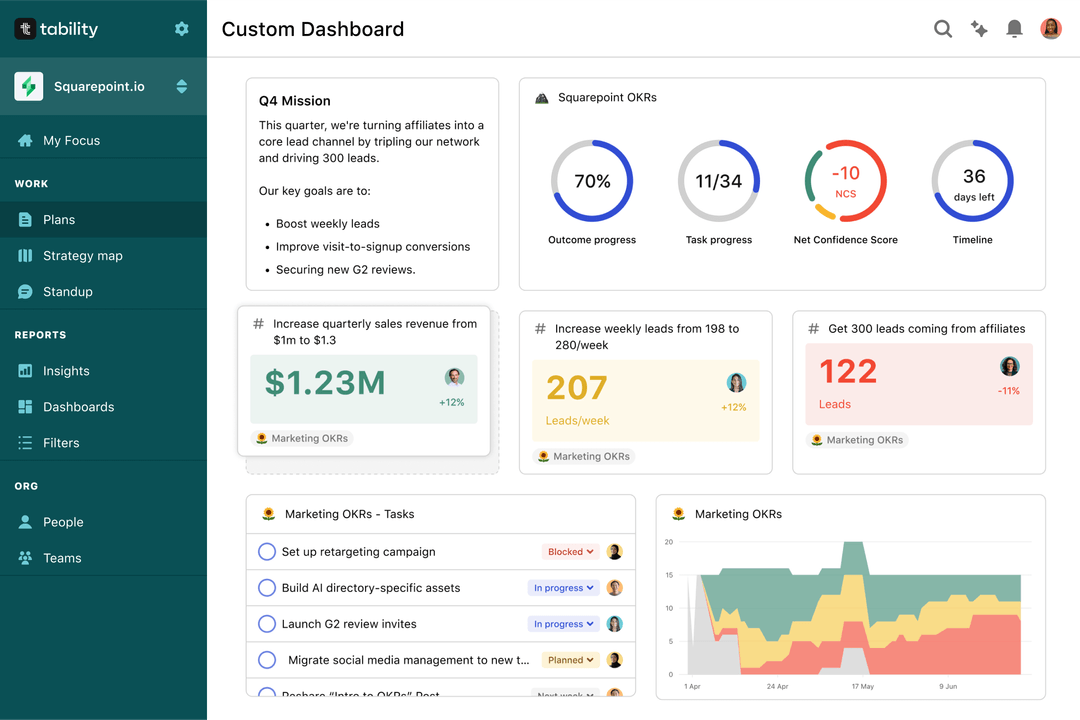
Your quarterly OKRs should be tracked weekly if you want to get all the benefits of the OKRs framework. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Spreadsheets are enough to get started. Then, once you need to scale you can use Tability to save time with automated OKR dashboards, data connectors, and actionable insights.
How to get Tability dashboards:
- 1. Create a Tability account
- 2. Use the importers to add your OKRs (works with any spreadsheet or doc)
- 3. Publish your OKR plan
That's it! Tability will instantly get access to 10+ dashboards to monitor progress, visualise trends, and identify risks early.
More It Trainer OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to excel in all elements of English class
OKRs to lower unvalued inventory by 10%
OKRs to implement SOCs playbooks for abnormal activities
OKRs to uncover and articulate the 'as-is' process accurately
OKRs to establish a formidable brand presence
OKRs to drive adoption of environmental policies by the National Park Service